Dr. David Edward Marcinko; MBA MEd
SPONSOR: http://www.HealthDictionarySeries.org
***
***
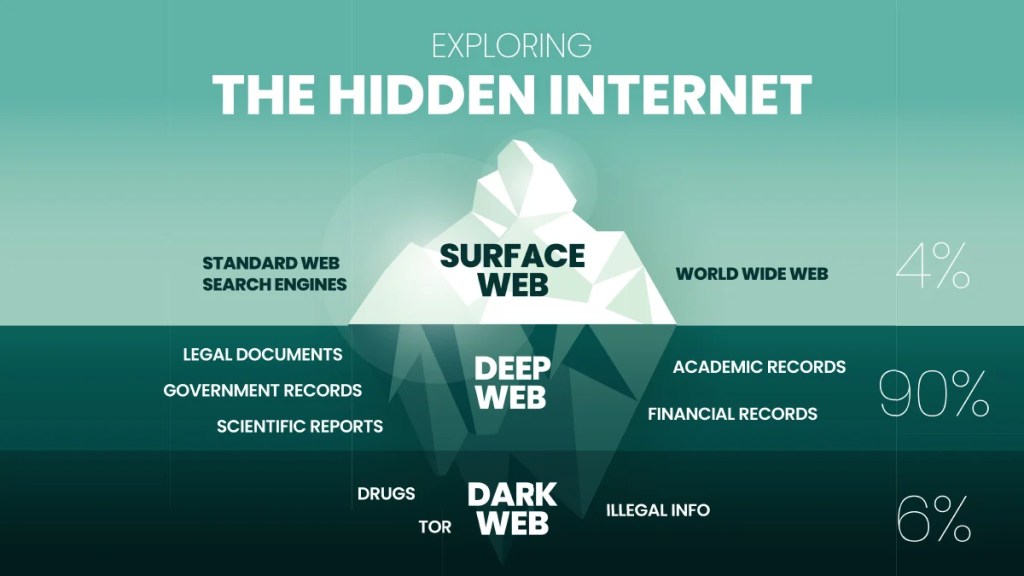
An Explanation of What an IP Address Is
An Internet Protocol (IP) address is a numerical identifier assigned to network interfaces participating in an IP‑based network. It functions as the cornerstone of packet‑switched communication, enabling devices to locate, identify, and exchange data across interconnected networks. At a technical level, an IP address encodes both host identity and network topology, allowing routers to forward packets efficiently through hierarchical addressing structures.
IP Address Structure and Protocol Versions
The two dominant versions of the Internet Protocol—IPv4 and IPv6—define the format and semantics of IP addressing.
IPv4, defined in RFC 791, uses a 32‑bit address space. These 32 bits are typically represented in dotted‑decimal notation, divided into four octets. The address space provides possible addresses, roughly 4.3 billion. IPv4 addresses are logically divided into network and host portions, historically using classful addressing (Classes A, B, C), though modern networks rely on Classless Inter‑Domain Routing (CIDR). CIDR allows arbitrary prefix lengths, expressed as a suffix such as /24, enabling more efficient allocation and route aggregation.
IPv6, defined in RFC 8200, expands the address space to 128 bits, represented in eight groups of hexadecimal values separated by colons. The enormous address space— possible addresses—supports hierarchical routing, stateless address autoconfiguration (SLAAC), and built‑in support for multicast and anycast addressing. IPv6 eliminates broadcast traffic entirely, replacing it with more efficient multicast mechanisms.
Address Types and Scopes
IP addresses can be categorized by scope and function:
- Unicast: Identifies a single network interface. Most traffic on the internet is unicast.
- Multicast: Identifies a group of interfaces; packets are delivered to all group members.
- Broadcast (IPv4 only): Targets all hosts on a local network segment.
- Anycast (primarily IPv6): Assigned to multiple interfaces; packets are routed to the nearest instance based on routing metrics.
Additionally, addresses can be public (globally routable) or private (RFC 1918 for IPv4, Unique Local Addresses for IPv6). Private addresses require Network Address Translation (NAT) to communicate with the public internet, a workaround that became essential due to IPv4 exhaustion.
Static vs. Dynamic Assignment
IP addresses may be assigned statically or dynamically:
- Static addressing involves manual configuration and is common for servers, routers, and infrastructure requiring predictable reachability.
- Dynamic addressing uses the Dynamic Host Configuration Protocol (DHCP). DHCP automates address assignment, lease renewal, and configuration of parameters such as default gateways and DNS servers.
In IPv6 networks, dynamic assignment may use DHCPv6 or SLAAC. SLAAC allows hosts to generate their own addresses using router advertisements and interface identifiers, reducing administrative overhead.
Routing and Packet Delivery
IP addresses are integral to routing—the process by which packets traverse networks. When a host sends a packet, it encapsulates data in an IP header containing source and destination addresses. Routers examine the destination address and consult their routing tables to determine the next hop. Routing protocols such as OSPF, BGP, and IS‑IS maintain these tables by exchanging topology information.
The hierarchical nature of IP addressing enables route aggregation, reducing the size of global routing tables. For example, a provider may advertise a single /16 prefix representing thousands of customer networks.
DNS and Address Resolution
Human‑readable domain names must be translated into IP addresses before communication can occur. The Domain Name System (DNS) performs this translation. When a user enters a URL, the system queries DNS resolvers, which return the corresponding A (IPv4) or AAAA (IPv6) records.
On local networks, the Address Resolution Protocol (ARP) maps IPv4 addresses to MAC addresses. IPv6 uses Neighbor Discovery Protocol (NDP) for similar functionality, leveraging ICMPv6 messages.
Security and Privacy Considerations
IP addresses reveal network topology and can expose approximate geographic location. Attackers may use them for reconnaissance, scanning, or targeted attacks. Techniques such as NAT, VPNs, and IPv6 privacy extensions help mitigate exposure by masking or rotating interface identifiers.
Conclusion
An IP address is far more than a simple identifier; it is a fundamental component of the Internet Protocol suite, enabling routing, addressing, and communication across global networks. Its structure, allocation mechanisms, and interaction with routing and resolution protocols form the backbone of modern digital infrastructure. As the internet continues to scale and diversify, the role of IP addressing—particularly IPv6—remains central to the performance, security, and scalability of global communication systems.
COMMENTS APPRECIATED
SPEAKING: Dr. Marcinko will be speaking and lecturing, signing and opining, teaching and preaching, storming and performing at many locations throughout the USA this year! His tour of witty and serious pontifications may be scheduled on a planned or ad-hoc basis; for public or private meetings and gatherings; formally, informally, or over lunch or dinner. All medical societies, financial advisory firms or Broker-Dealers are encouraged to submit an RFP for speaking engagements: CONTACT: Ann Miller RN MHA at MarcinkoAdvisors@outlook.com -OR- http://www.MarcinkoAssociates.com
Like, Refer and Subscribe
***
***
Filed under: "Ask-an-Advisor", Experts Invited, Glossary Terms, Marcinko Associates, Retirement and Benefits | Tagged: ARP, BGP, CIDR, cybersecurity, david marcinko, DHCP, DNS, internet protocol, IP, IP address, IPv4, IPv6, NDP, networking, RFC, risk, Risk Management, routing, routing protocols, security, Technology | Leave a comment »