By Staff Reporter and and A.I.
***
***
The Dark Web: A Hidden Layer of the Internet
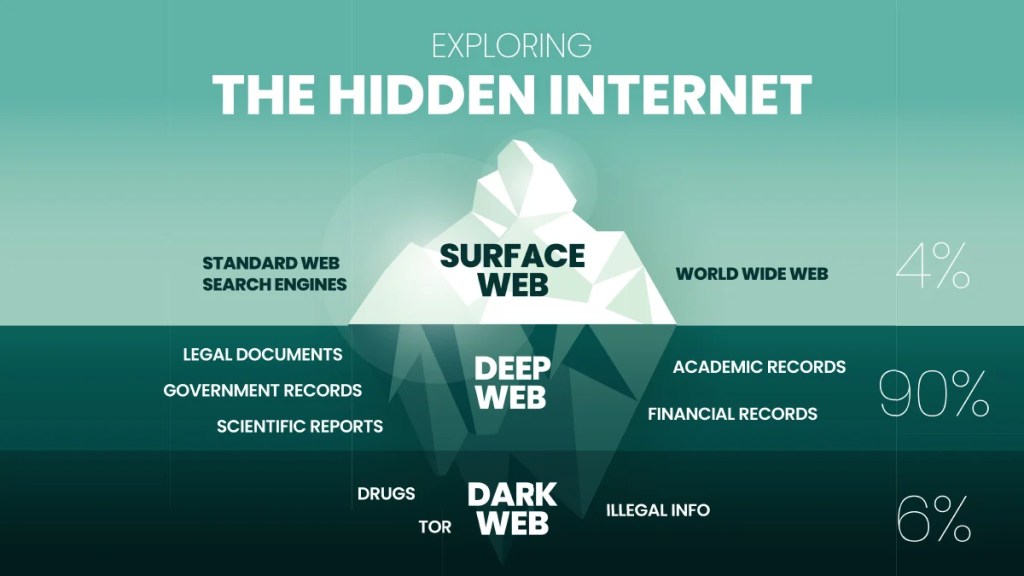
The internet is often described as an iceberg. The surface—what most users interact with daily—is the “surface web,” consisting of indexed websites accessible through standard search engines like Google or Bing. Beneath this lies the “deep web,” which includes content not indexed by search engines, such as private databases, academic journals, and password-protected sites. But even deeper still is the “dark web,” a hidden realm of the internet that requires special software to access and is often shrouded in mystery and controversy.
The dark web is accessible only through anonymizing networks like Tor (The Onion Router), which mask users’ identities and locations. This anonymity is both its greatest strength and most significant risk. Originally developed by the U.S. Navy to protect sensitive communications, Tor now serves as a gateway to a decentralized network where users can operate beyond the reach of traditional surveillance and censorship.
While the dark web is often associated with illegal activity—such as drug trafficking, weapons sales, and identity theft—it also serves legitimate purposes. Journalists, whistleblowers, and political dissidents in oppressive regimes use it to communicate safely and share information without fear of retaliation. Platforms like SecureDrop allow sources to submit documents anonymously to media outlets, helping expose corruption and injustice.
However, the dark web’s reputation is largely shaped by its criminal underbelly. Marketplaces like Silk Road, AlphaBay, and Hansa have been notorious for facilitating illicit trade. These platforms often use cryptocurrencies like Bitcoin to enable anonymous transactions. Law enforcement agencies around the world have responded with crackdowns, leading to arrests and shutdowns, but new sites frequently emerge to take their place.
The dual nature of the dark web presents a complex ethical dilemma. On one hand, it offers a haven for free speech and privacy in an increasingly monitored digital world. On the other, it enables activities that threaten public safety and national security. Governments and cybersecurity experts continue to grapple with how to regulate this space without infringing on civil liberties.
Understanding the dark web requires a nuanced perspective. It is not inherently evil, nor is it entirely virtuous. Like any tool, its impact depends on how it is used. As technology evolves, so too will the dark web, and society must remain vigilant in balancing the need for privacy with the imperative to prevent harm.
TOR: https://www.torproject.org/about/history/
In conclusion, the dark web is a multifaceted component of the internet that challenges our notions of freedom, security, and ethics. It serves as both a refuge for the vulnerable and a playground for the unscrupulous. As we navigate this hidden frontier, education and awareness are key to ensuring that its potential is harnessed responsibly.
COMMENTS APPRECIATED
Like, Refer and Subscribe
***
***
Filed under: "Ask-an-Advisor", business, Information Technology, Risk Management | Tagged: Alpha Bay, Bitcoin, cybersecurity, dark web, deep web, digital marketing, Hansa, hidden internet, internet, onion router, search engines, SecureDrop, seo, silk road, surface web, Technology, Tor, world wide web, www | Leave a comment »