***
***
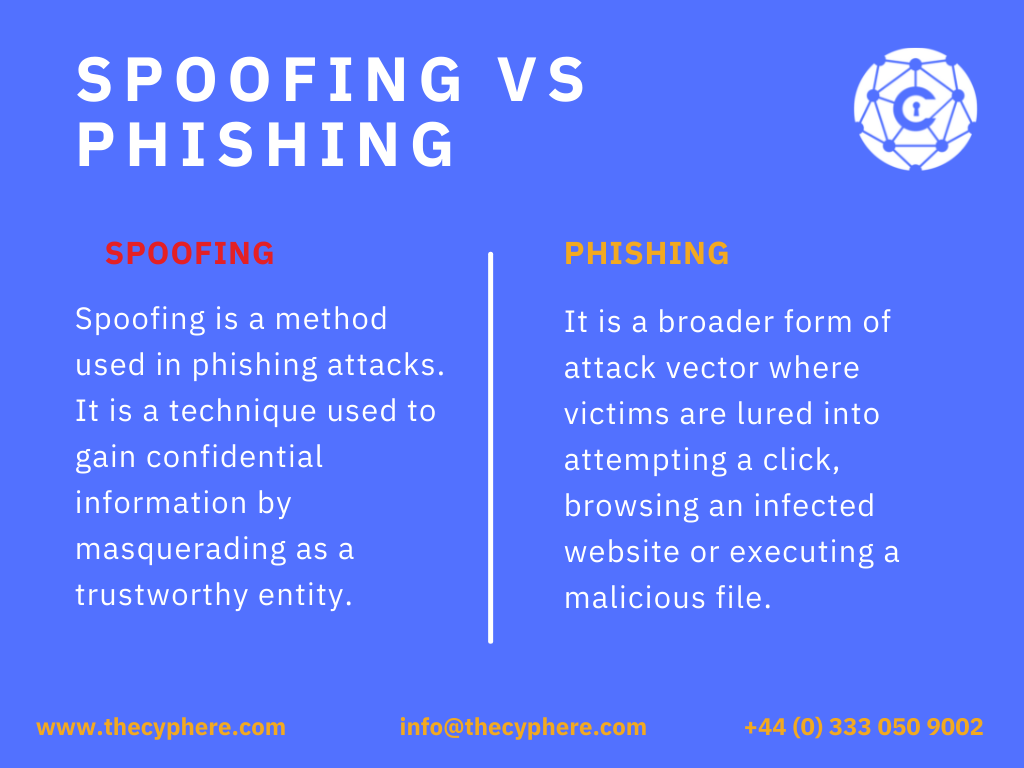
Smishing is a form of phishing that uses Short Message Service (SMS), commonly known as text messages, instead of email. Typically, the scammer poses as a legitimate institution, such as a bank, a service provider or a reputed company. The text message they send creates a sense of urgency or threatens consequences if the victim doesn’t respond immediately. It downloads malware on the phone or includes a link to a fraudulent website designed to look like the legitimate organization’s site. When victims reach that site they are tricked into entering their personal information.
Seven Types of Smishing Scams
1. Impersonation Scams: The attacker pretends to be a known organization or individual. The attack could be via a message pretending to be from a bank, government agency or a reputable company.
2. Tech Support Scams: Attackers pose as representatives from tech companies, claiming that the victim’s device or account has been compromised and that they need sensitive data to fix the problem.
3. Account Suspension Scams: These messages claim that an account (bank account, social media or any other service) has been suspended and prompt the victim to verify their identity by providing sensitive information.
4. Missed Delivery Scams: Attackers send messages claiming that the victim has missed a package delivery, and they need to provide personal details or a fee to reschedule the delivery.
5. Prize or Lottery Scams: Messages claiming that the victim has won a prize or a lottery, and they need to provide personal details or make a payment to claim the winnings.
6. Charity Scams: In these attacks, scammers impersonate a charitable organization, asking for donations, usually following a large-scale disaster or during holiday seasons.
7. Malware Link Scams: Messages containing a link, which when clicked, installs malware on the victim’s device, allowing the attacker to steal information or gain control over the device.
Attackers are constantly innovating and finding new ways to exploit human trust, so it’s crucial to be skeptical of any unsolicited or unexpected message that asks for sensitive information or prompts to click a link.
COMMENTS APPRECIATED
Refer and Subscribe
***
***
Filed under: Ethics, Glossary Terms, Information Technology, LifeStyle, mental health | Tagged: mental health, phishing, scam, scams, secure message service, security, short message service, smish, smishing, smishing scams, smishing., SMS | Leave a comment »