By Staff Reporters
***
***
What is Honeypot?
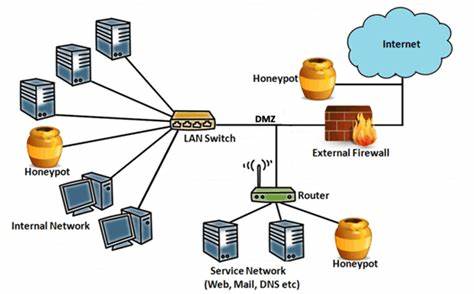
A Honeypot is a network-attached system used as a trap for cyber-attackers to detect and study the tricks and types of attacks used by hackers. It acts as a potential target on the internet and informs the defenders about any unauthorized attempt at the information system.
Honeypots are mostly used by large companies and organizations involved in cybersecurity. It helps cybersecurity researchers to learn about the different types of attacks used by attackers. It is suspected that even cyber criminals use these honeypots to decoy researchers and spread wrong information. The cost of a honeypot is generally high because it requires specialized skills and resources to implement a system such that it appears to provide an organization’s resources while still preventing attacks at the back end and access to any production system.
Advantages of Honeypot
- Acts as a rich source of information and helps collect real-time data.
- Identifies malicious activity even if encryption is used.
- Wastes hackers’ time and resources.
- Improves security.
Disadvantages of Honeypot
- Being distinguishable from production systems, it can be easily identified by experienced attackers.
- Having a narrow field of view, it can only identify direct attacks.
- A honeypot once attacked can be used to attack other systems.
- Fingerprinting(an attacker can identify the true identity of a honeypot ).
What is Honeynet?
A honeynet is made up of two or more honeypots connected via a network. Having a linked network of honeypots can be beneficial. It allows organizations to trace how an attacker interacts with a single resource or network point while also monitoring how a hacker moves between network points and interacts with numerous points at the same time.
The goal is to induce hackers to believe that they have successfully breached the network. Having more false network destinations makes the arrangement appear more realistic.
COMMENTS APPRECIATED
Refer, Like and Subscribe
***
***
Filed under: Experts Invited, Glossary Terms, Information Technology, LifeStyle, Research & Development, Risk Management | Tagged: AI, computer networks, computer security, cyber hacks, Cyber Security, cybersecurity, HIT, honeynet, honeynets, honeypot, honeypots, Information Technology, IT, security, Technology | Leave a comment »