For the Insurance, Healthcare, Education, and Financial Services Sectors
[By Egress Software Technologies]
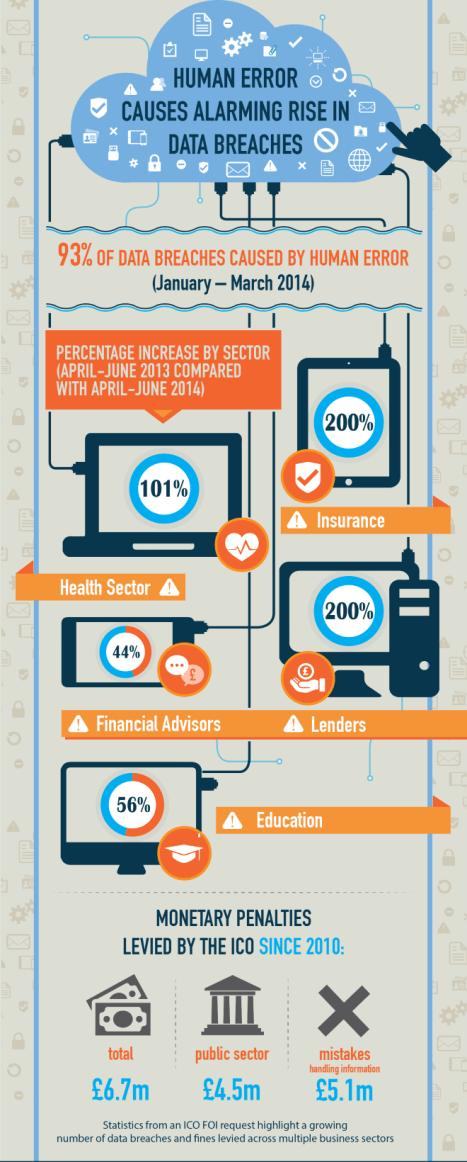
Human error causes alarming rise in the number of data breaches and resulting monetary penalties, according to ICO FOI request carried out by Egress Software Technologies.
***
***
[Blame Human Error – Not Hardware Bugs]
***
More:
- How Expensive are Healthcare Data Breaches?
- Protected Health Information Data Breaches
- Don’t Hide a Security Breach if You Can’t Do the Time
Conclusion
Your thoughts and comments on this ME-P are appreciated. Feel free to review our top-left column, and top-right sidebar materials, links, URLs and related websites, too. Then, subscribe to the ME-P. It is fast, free and secure.
Speaker: If you need a moderator or speaker for an upcoming event, Dr. David E. Marcinko; MBA – Publisher-in-Chief of the Medical Executive-Post – is available for seminar or speaking engagements. Contact: MarcinkoAdvisors@msn.com
OUR OTHER PRINT BOOKS AND RELATED INFORMATION SOURCES:
- PRACTICES: www.BusinessofMedicalPractice.com
- HOSPITALS: http://www.crcpress.com/product/isbn/9781466558731
- CLINICS: http://www.crcpress.com/product/isbn/9781439879900
- ADVISORS: www.CertifiedMedicalPlanner.org
- FINANCE: Financial Planning for Physicians and Advisors
- INSURANCE: Risk Management and Insurance Strategies for Physicians and Advisors
- Dictionary of Health Economics and Finance
- Dictionary of Health Information Technology and Security
- Dictionary of Health Insurance and Managed Care
Filed under: iMBA |

















Ponemon Institute and IBM
According to a research report on the costs of data breach conducted by the Ponemon Institute and sponsored by IBM , the numbers for 2014 are disheartening. It’s unsurprisingly and recommend reading if you have organizational responsibility or input on these issues, including a board of directors position.
Here’s a look at just a fraction of what they report:
1. Breaches have a higher overall cost than in the past;
2. More customers leave a business after a breach than before;
3. The costs of redress are higher than before including remedial action;
4. The average cost per record exposed by malicious activity is substantially greater than in our example above; they put it at $246 per record.
Ike Devji JD
LikeLike
Three Components of Security
The three classic components of information security are confidentiality, integrity, and availability. Donn B. Parker, a pioneer in the field of computer information protection, added possession, authenticity, and utility to the original three.
These six attributes of information that need to be protected by information security measures can be defined as follows:
• Confidentiality: The protection and ethics of guarding personal information — for example, being cognizant of verbal communication leaks beyond conversation with associated healthcare colleagues.
• Possession: The ownership or control of information, as distinct from confidentiality — a database of protected health information (PHI) belongs to the patients.
• Data integrity: The process of retaining the original intention of the definition of the data by an authorized user — this is achieved by preventing accidental or deliberate but unauthorized insertion, modification or destruction of data in a database. Make frequent backups of data to compare with other versions for changes made.
• Authenticity: The correct attribution of origin — such as the authorship of an e-mail message or the correct description of information such as a data field that is properly named. Authenticity may require encryption.
• Availability: The accessibility of a system resource in a timely manner — for example, the measurement of a system’s uptime. Is the intranet available?
• Utility: Usefulness; fitness for a particular use — for example, if data are encrypted and the decryption key is unavailable, the breach of security is in the lack of utility of the data (they are still confidential, possessed, integral, authentic and available).
Richard Mata MD MIS
LikeLike
Health Data Breaches Sow Confusion, Frustration
According to Charles Ornstein, one consumer was the victim of hacking attacks on two different health insurers; a company’s privacy officer didn’t realize that health insurer Anthem even had her data.
http://www.propublica.org/article/health-data-breaches-sow-confusion-frustration?utm_source=et&utm_medium=email&utm_campaign=dailynewsletter&utm_content=&utm_name=
“It gives you a new perspective when you’re actually one of the folks whose data is disclosed.”
Soloman
LikeLike